Subscribe to get my latest posts straight to your inbox, no noise!
Generative AI has taken the world by storm, offering endless opportunities for innovation. But as with any new technology, there are plenty of pitfalls to avoid. In this post, I dive into the current state of AI startups, shedding light on what works, what doesn't, and why. If you're looking...
Why GenAI Will NOT Replace Software Engineers
For now...
GenAI systems are becoming more and more capable of performing complex cognitive tasks that were once thought to be uniquely human. In particular, LLMs are proven to be very good at writing code. With all the buzz around GenAI replacing software engineers, are our jobs really at risk? In this...
The Not-So-Strange Case of Cargo Cult in Computer Science Research
Are we mimicking scientific progress without true innovation?
Arguably, computers and faster communication systems have changed the world more than any other technology. Yet there have been many scientific failures along the way, some prominent, many minor, and a widening gap between aspirations and reality. This article discusses the problem of pseudoscience in computer science. I discuss Richard...
Some Things to Remember Before Acting Pretentiously
And a few personal thoughts on the value of sincere humility
A few days ago, I had a conversation about my ambitions for the future. At one point, I mentioned that I would like to achieve something remarkable and gain public recognition for it. In retrospect, my answer was quite pretentious. After reflecting deeply on this topic, I realized that what...
The Last Paper's Myth
A tale of contending interests
The "last paper myth" emerges once academic supervisors realize that a student is about to earn their PhD and leave. It's one last stronghold for supervisors to capitalize on the time and effort they have invested in their students' scientific training. This relentless push not only detracts from the true...
On the Rise, Decline, and Persistence of Web Technologies
From Static HTML Pages to WebAssembly
The web is (arguably) the only tech platform that has been continuously transformed and evolved at a global scale over the last 30 years. How was this possible? What can we learn from the past technical mistakes and successes? Over the years, I have witnesses the emergence of various web...
The Most Relevant Technical Skill in My Career
It isn't Java coding
Have you ever wonder which is most relevant technical skill in your career? It's not necessarily a programming language or the latest framework. For me, it is Exploratory Data Analysis (EDA). Why? Because being able to manipulate and find relevant information from various data sources has opened me doors to...
AI Doesn't Make Me the Same Coffee
And it doesn't understand wine either
Advancements in AI are set to transform the way we interact with the world, offering increased free time and enhanced capabilities. However, if not carefully managed, AI poses risks such as reducing human experiences and potentially becoming a significant social issue.
Building and Leveling Up a Computer Scientist Résumé
My personal take to stand out from the crowd
Résumés have become fundamental for personal branding. They not only list qualifications but also reflect an individual's professional identity, career goals, and unique value proposition. In today's competitive job market, a well-crafted résumé can make all the difference in securing a job interview. This article covers how to build the...
Revisiting Ken Thompson’s Reflection on Trusting Trust
One of the most chilling ideas in cybersecurity's history
Creating software entirely from scratch is impractical today. Every component, library, and tool we use in software development relies on open source libraries and compilers. In his talk "Reflections on Trusting Trust," Ken Thompson brilliantly demonstrates that "You cannot trust code that you did not totally created yourself." I find...
How I Peer Review Research Papers
My reviewer flow, focused template, and personal tips
In this blog post, I share my experiences and personal approach when peer-reviewing research papers in the field of software engineering. My focus is on delivering good peer reviews, fast and effectively. I give my template and provide generalizable examples of good and bad reviews. After reading this post, as...
My Ultimate Terminal Customizations for Windows
Another guide
This post describes the tools I use to resemble my macOS terminal customizations on Windows. This includes the fonts that I choose for the Windows Terminal app, an enhanced PowerShell, and the installation of third-party tools like Oh My Posh. I've found that these small improvements make me a happier...
Surviving the AI Revolution as a Software Engineer
Is there still any hope?
The next wave of extremely powerful and specialized AI models is coming, and it will likely revolutionize software engineering as we know it. As developers, we need to get the skills to surf the wave and keep our jobs. As with every technological breakthrough, AI will create new jobs and...
A Prime on Public Key Infrastructure
How do we trust each other in the digital era?
This article delves into symmetric and asymmetric encryption, as the building blocks of Public Key Infrastructure (PKI). It describes how PKI allows safeguarding the authenticity and security of digital communications across the internet.
My PhD as a Comic
The time when I became a superhero
At the end of my PhD journey, I was lucky enough to be surrounded by professional software artists. Together, we created a comic to make the ideas of my PhD thesis more accessible and engaging to the non-tech audience. In this article, I share the comic and the story behind...
How to Give a Great Technical Presentation
Here's what I've learned
I believe that the secret to delivering a great technical presentation is feeling in control. This enables the confidence to communicate effectively and it also helps to be perceived as an expert. In this article, I share the tips and tricks I've learned from my own flaws, and also from...
Prompting is All We Need
Is this the end of software engineering as we know it?
Today's AI-powered systems can generate code cheaper and faster than developers. The new era of automated text generation has come to us developers. And with it, there comes a new batch of fresh challenges. Fortunately, AI still craves human guidance. Effective prompt engineering is revolutionizing software development as we know...
Let's Face It: Paper Figures Are Always Subject to Change
The story of a single figure
As a researcher, I have learned that the process of creating figures is a journey of discovery, a process of refinement, and a crucible of critique. This article provides insights into the transformations that a particular figure undergo throughout the research process (before publication).
Securing a Permanent Job in Sweden Before Completing My PhD
My personal experiences and tips
In this article, I share insights about my transitional journey when moving from academia to industry, having secured a position at a big Swedish company prior to completing my PhD in Computer Science. My goal is to provide some insights, inspiration, and hope to my colleagues who find themselves contemplating...
Data Serialization/Deserialization in Java With Apache Avro
Getting started
Apache Avro stands as the go-to data serialization framework for efficient binary data streaming. In this article, I cover the main features of Avro and why/when/how to use it for serialize and deserialize data files in Java.
How to Write a Good Cover Letter for a Research Paper
Quick an easy
It's a common practice in academic journals to ask authors to write a short cover letter to the editor. In this post, I share my experience writing cover letters for academic journals, along with useful tricks and tips that I've found along the way.
The True Value of Attending Academic Conferences
It's not only about the technical content
I recently attended the 29th edition of ESEC/FSE 2022 in Singapore. This was my first time participating in a big academic conference (in real-life). In this blog post, I share my experiences, with a focus on what I think is the actual value of attending these kinds of events.
The Execution Lifecycle of a Java Application
Or... what happens when you run a Java program?
This blog post describes in details what happens when executing a Java application. After reading this post, you will understand the execution lifecycle of a Java application and the activities performed by the JVM during the execution phase.
On the Parkinson's Law of Triviality for Computer Science Researchers
It must stop!
The Parkinson's Law explains how we spend disproportionate amounts of time discussing trivialities instead of focusing on solving core problems. In the research context, this behavior is considered unproductive because it drains the researchers' energy on matters of little or null impact. This behavior can also be considered a form...
Why Debloating Third-Party Software?
The case of the Log4j vulnerability
The Log4j vulnerability is an example of the dangers of massively reusing third-party libraries. This article discusses how software debloating can make a difference by reducing the attack surface of applications, removing unnecessary code from software libraries.
My Ultimate Terminal Customizations for macOS
A guide
There is a common belief that top-class software developers can do their job without ever abandoning the terminal. This blog post is a how-to guide for you (and my future self) to configure the terminal in a way so that we will enjoy every command typed on it.
No One Cares About Your Research!
A comfortable truth
Doing a PhD is sometimes a very stressful journey. I believe this stress is unnecessary, as it primarily results from students taking science too seriously. They genuinely believe that others are continuously evaluating the quality of their research. But this is very far from being true. In practice, no one...
The Dynamic Features of Java
A long-standing challenge for static analyzers
The existence of dynamic features built in the language allows Java developers to transform their program executions at runtime dynamically. However, these features in most Java programs are a fundamental problem for static analysis tools that rely on precise call-graph construction. Notably, the GraalVM compiler relies on points-to analysis to...
Inversion of Control and Dependency Injection in Java
The holy grails of modern enterprise Java frameworks
This blog post explains Inversion of Control and Dependency Injection in Java. These concepts are the backbone of modern enterprise Java frameworks.
AOT vs. JIT Compilation in Java
Which one is better?
AOT compilation, supported by the GraalVM compiler, seems to be the future for Java and the programming languages that compile to JVM bytecode. But what is the difference between compiling source code using a JIT compiler w.r.t using an AOT compiler? This post explains the difference between these two approaches....
How to Write a Good Revision Letter For an Academic Paper
My system to address major revisions and get my papers accepted
Dealing with a major revision is a challenging process in the life of doctoral students. In this post, I share my personal system and some useful resources that may help you to navigate the academic revision process with panache.
Staying in Academia: How PhD Profiles are Evaluated?
An overview
For those who decided to stay in academia, achieving a position as a tenured professor is not easy, to say the least. There are several evaluation layers to pass before reaching this position, so it is better to be prepared. Research profiles are be carefully evaluated before being accepted or...
Bus Factor: A Human-Centered Risk Metric in the Software Supply Chain
Public transportation may become hellish
What would happen to a software project if some of its developers were suddenly hit by a bus? The “bus factor” measures the amount of spread of knowledge within a dev team so that the project can survive the most drastic loss of personnel. Managers should keep an eye on...
How to Write a Good Paper Rebuttal
A practical guide
My conference paper was rejected. Is it worth writing a rebuttal? This post answers this question and presents practical guidelines to write an excellent rebuttal.
How to Track the Progress of a Research Project
My methodology based on the weekly delivery of verifiable artifacts
Academic research is a demanding activity in constant change and evolution. Consequently, tracking the progress of a research project is challenging. This post describes my methodology to address this particular problem.
Encoding, Encryption, Hashing, and Obfuscation in Java
From concepts to code
The concepts of encoding, encryption, hashing, and obfuscation are often mistakenly confused or taken as similar (which is even worse). Let's clarify this matter and see some Java code examples of practical applications.
SIGBOVIK: The Ig Nobel for Academics and Computer Science Researchers
The most wanted proceedings for fruitful procrastination
The SIGBOVIK humor-filled conference is the most disruptive Computer Science academic conference I've ever seen. This exceptional venue allows demystifying complicated concepts through sarcasm and mockery while getting away from the rigors of standard academic research.
How to Set Up A Blockchain Network With Hyperledger Besu
Look mom, I'm running my own blockchain!
If you are a Java developer interested in cryptocurrencies and blockchain-related technologies, you should probably have heard about Hyperledger Besu, the official Java client of the Ethereum blockchain. In this post, we're going to set up a production-ready Ethereum client using Besu.
How I Overcome Writer's Block When Preparing a Research Paper
My bulletproof approach
Writing a research paper can be a tremendous challenge, even for experienced researchers. I've faced the so-called writer's block many times, especially when starting the writing process. Fortunately, with time I've developed personal systems that allow me to deal with this particular issue.
Seven Reasons to Go For a PhD In Computer Science
The good, the bad, and the ugly
Starting a PhD in Computer Science is a serious decision that literally changes your life. There are many motivations to choose this career path. This post outlines seven reasons for pursuing a PhD in Computer Science. It stresses the importance of clear motivations due to the significant time investment required....
The Software Supply Chain
A quick look at the modern software production landscape
The software supply chain encompasses all technologies and processes involved in moving code from development to production. It heavily relies on third-party components, which introduces significant security and maintenance risks. Supply chain attacks occur when malicious actors compromise these components, making entire infrastructures vulnerable, as seen in incidents like the...
Design For Microservices!
An easy way to boost the popularity of your open-source projects
The microservices architecture has gained significant momentum in the last years. Modularity, scalability, and elasticity are some of its essential characteristics. If you have an open-source project, you should consider designing it to be microservices friendly. The market will eventually reward you for that.
Configuring Remote Connections in Unix-Based Systems Using SSH
A noob's guide
This practical guide will show you how to configure a remote connection in Unix-based systems. You will learn how to create RSA keys and use SSH to configure the connection from the terminal.
What Does It Take to Become a Software Architect?
A matter of responsibilities
The software architect is the person who has the authority to make the technical decisions regarding the architecture of a software project and stay responsible for them. This position requires a high level of authority and responsibility. This post explains what these two words actually mean and discusses the necessary...
Hermit Programmers are Dead
Don't call yourself a programmer anymore
The era of the lone, isolated programmer is coming to an end. With the rise of cloud computing, AI, and automation, programmers must evolve into versatile software engineers, embracing collaboration, communication, and a broader skill set. This post explores why programmers who don't diversify their skills or adapt to new...
Replace the Disqus Commenting System on Your Blog
GitHub-based open-source alternatives are better
Disqus has started forcing unwanted ads on free users, making it less appealing for bloggers and small businesses. This post explores open-source alternatives like Giscus, a GitHub-based commenting system that offers a lightweight, ad-free, and developer-friendly experience. Here is a guide on how to replace Disqus on your blog and...
Book Review: The PhD Grind
A tale of perseverance and learning from failure
Philip Guo's "The PhD Grind" offers a candid, unfiltered account of his PhD journey in Computer Science. The book provides invaluable insights into the challenges, failures, and personal growth that come with pursuing a doctorate. This review highlights my reflections after reading it. I paid special attention to the emotional...
The Fork/Join Java framework
Boosting performance through parallelization
The Fork/Join framework in Java simplifies parallel programming by allowing developers to leverage multiple processor cores without manually managing threads. This post introduces the key concepts of this framework, including task splitting (fork) and result combining (join). I also provide practical examples using RecursiveAction and RecursiveTask for parallelizing tasks. By...
Use Custom LaTeX Macros to Boost Your Writing Productivity
Forget about these annoying numerical glitches in your LaTeX document
In this blog post, I describe how I use LaTeX macros to boost my writing productivity by automating repetitive tasks such as formatting and number computations. I explain how to create custom commands for common tasks like abbreviations, author notes, formatting and computing numbers, percentages, and ratios, as well as...
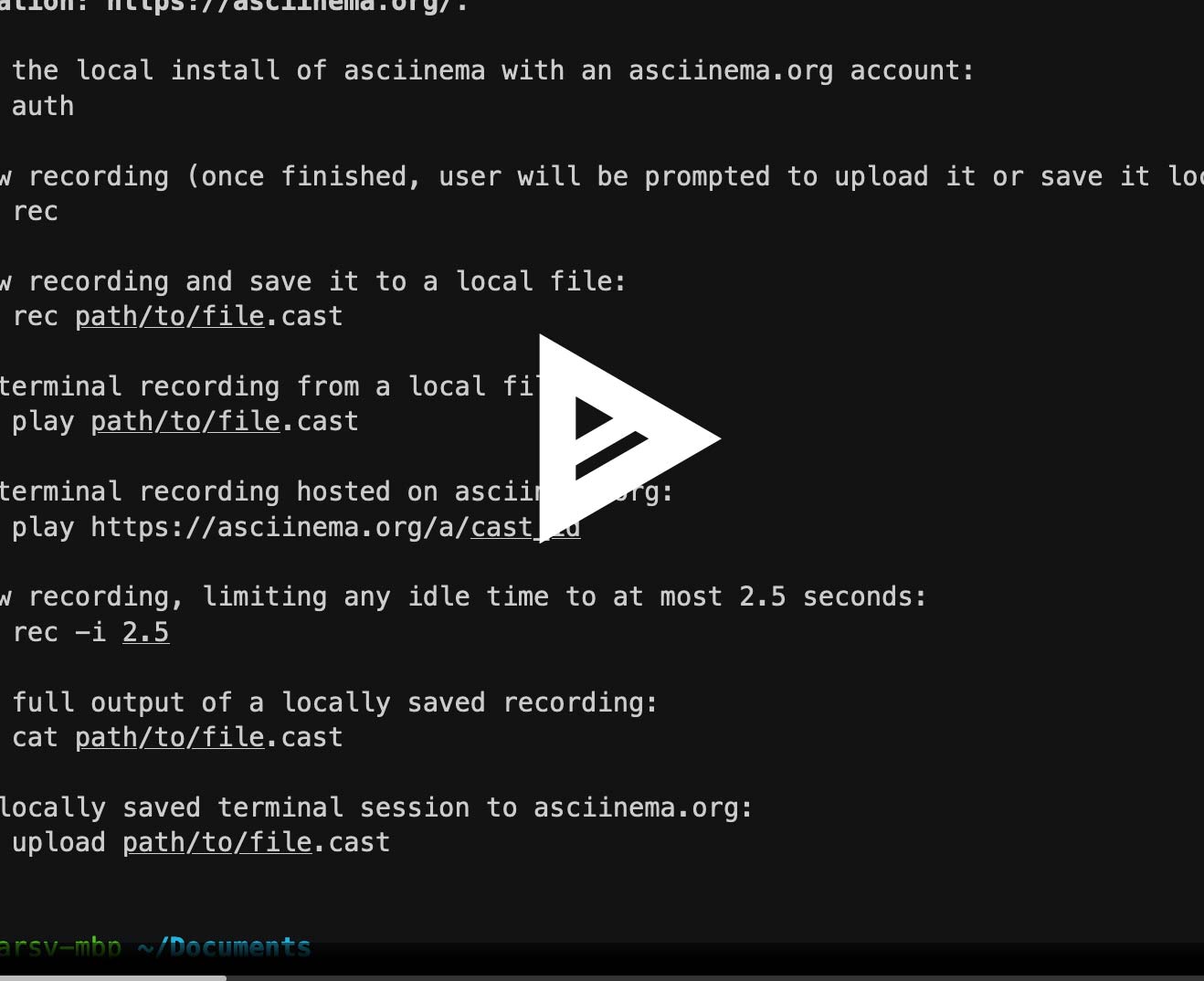
Enhance Your Readme With Asciinema
How to create beautiful terminal recordings that your users will love
This blog post explains how to use Asciinema to create and share beautiful terminal recordings, particularly for enhancing README files on GitHub. It walks through the steps of recording a terminal session with Asciinema, converting the CAST file into a GIF using asciicast2gif for Markdown compatibility, and embedding the recording...
Clean Commit Messages
The way I like to write them
Writing clean commit messages is a craft that benefits the project in the long run. It enhances collaboration, eases maintenance, and keeps the project history informative and navigable. At the individual level, a commit message is a reflection of professionalism and attention to detail. This article highlights some of the...
Dynamic Programming by Example
A handful of representative problems solved in Java
Dynamic programming (DP) is one of the most basic and, at the same time, challenging programming paradigms. This post covers its core concepts through two key strategies: memoization and tabulation. I use a series of representative problems (e.g., Fibonacci, Grid Traveler, and Can Sum) to demonstrate how these strategies simplify...
Shortening the Distance Between Academia and Industry
An imperative need of researchers
Presenting research work to industrial engineers is essential for the sustainability of the whole research business. In this post, I emphasize the need for researchers to engage more actively with the local industry by sharing their findings, fostering collaborations, and addressing industry-relevant challenges. By doing so, researchers can demonstrate the...
Empirical Software Engineering Research Is Harder Than You Think
Trust me
Empirical software engineering (SE) research seemed straightforward to me a few years ago, but I discovered that it presents unique challenges that make it far more difficult than expected. In this post, I explain why tasks like formulating hypotheses, collecting data, and analyzing results in SE are more complex than...
How to Deploy a Simple Spring Boot Application in GCP
Getting started with Google Cloud Platform
Deploying a Spring Boot application to Google Cloud Platform (GCP) offers a streamlined way to bring your Java app to life on the web. This post is a step-by-step guide to deploying your application using both Google App Engine and Compute Engine. Whether you're looking for simplicity with App Engine...
The Producer-Consumer Pattern in Java Made Easy
An example using the BlockingQueue Java interface
The Producer-Consumer pattern is a powerful design strategy used to decouple the production of data from its processing, enabling parallelism and efficient data handling. This post is about how to implement this pattern in Java using the BlockingQueue interface, allowing for easy, thread-safe coordination between producers and consumers. This guide...
Diversity-Driven Software Debloat
Leveraging the wisdom of multiple coverage tools
Debloating Java artifacts can be challenging due to the limitations of code coverage tools in identifying unused code. In this post, I introduce a diversity-driven approach to software debloating that combines multiple coverage tools, including JaCoCo, JCov, Yajta, and the JVM class loader, to improve precision. I leveraged the strengths...
Unix Cmd Hacks
Boosting automation from the shell
Mastering the Unix command line can drastically boost your productivity and efficiency in software development. In this post, I share a collection of personal notes from the edX course "Unix Tools: Data, Software, and Production Engineering." This guide covers essential command-line tricks, from process automation to data manipulation, that every...
Recipes for Effective Academic Emailing
A template-based approach
Effective academic emailing is a skill every researcher and supervisor needs to master. In this post, I introduce a template-based approach to streamline email communication, enhancing productivity while maintaining professionalism. From initial introductions to assigning tasks and offering feedback, these templates will make managing the flood of academic emails a...
Deploying to Maven Central
A three-steps guide
Deploying to Maven Central is essential for sharing Java libraries with the world. In this post, I provide a detailed, step-by-step guide on how to deploy a software artifact to Maven Central, covering everything from setting up a Sonatype account to configuring POM files. By following this tutorial, you'll be...
The Cuban Revolution
My personal vision
The Cuban Revolution was a tremendous moment in the nation's history. It ended Batista's dictatorship but resulted in decades of Communist regime under Fidel Castro dictatorship. In this post, I provide a personal perspective on the Revolution's long-term effects, from the initial promise of social reforms to the harsh reality...
The Zip Slip Vulnerability Exploitation
Zip slip attacks
The Zip Slip vulnerability is a serious security flaw that exploits unprotected file extraction to perform directory traversal attacks. In this post, I explain how malicious archives exploit weak validation in extraction code, potentially allowing attackers to overwrite sensitive files and execute commands. I also provide an example of the...
The Practice of Teaching
The ultimate skill to learn
Teaching is an essential skill, whether you're a developer, researcher, or manager. In this post, I share my experience teaching the Quicksort algorithm using a blackboard. I highlight both the challenges and valuable lessons learned. From preparation tips to the importance of practice, my point is that honing your teaching...
Unnecessary Code
Clarifying the concept
Unnecessary code bloats software, consuming resources without contributing to functionality. In this post, I explore the complexities of identifying and removing unnecessary code, clarifying key distinctions between dead, unused, and bloated code. Learn how static and dynamic analysis, coupled with modern techniques like machine learning, are reshaping the process of...
A Starting Guide to Programming Contests
Is it worth it?
This post is about competitive programming, a practice that tests both mental agility and algorithmic skills. Drawing from my personal experience, I cover the essentials, from mastering key algorithms to building an effective training plan. I share practical tips, resource recommendations, and strategies that helped me become a better contestant....
Git Fundamentals
The must-know git commands for software developers
Git is the go-to version control system in software development, created by Linus Torvalds in 2005 for Linux kernel development. It's now an indispensable tool for tracking project history and managing versions. This post covers the key Git commands you need to streamline your development workflow.
How I Beat the IELTS Academic With Just a Month of Self-Training
My personal comments and suggestions
I recently passed the IELTS academic test, and it was not easy. This blog post dives deep into the strategies that helped me to complete every section of the exam (listening, reading, writing, and speaking) and beating the greatest enemy: time. I discovered that mastering the test structure and engaging...